|
Brussels, |
|
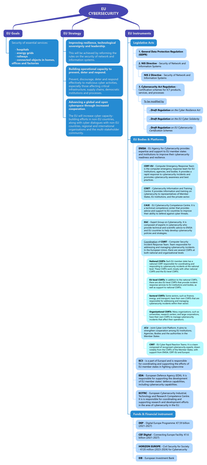
DIGITAL EUROPE
Cybersecurity
- EU Agency in charge is ENISA
The EU strategy
|
Cybersecurity is a crucial aspect of protecting systems and networks from information theft, damage, and disruption. The European Union has prioritized cybersecurity for many years and has allocated significant funding in its long-term budget for the 2021-2027 period to support:
The EU Cybersecurity Strategy aims to build resilience to cyber threats and ensure citizens and businesses benefit from trustworthy digital technologies. In December 2020, the European Commission and the High Representative of the Union for Foreign Affairs and Security Policy have presented a Joint Communication on EU Cybersecurity Strategy aimed at ensuring a global and open internet with strong safeguards where there are risks to security and the fundamental rights of people in Europe. |
The goal is to strengthen the EU's collective cybersecurity and response to cyberattacks by harnessing and strengthening all its tools and resources to be technologically sovereign. Governments, businesses and citizens share the responsibility of ensuring a cyber-secure digital transformation.
The goal covers the security of essential services, such as:
The goal covers the security of essential services, such as:
- hospitals
- energy grids
- railways
- a number of connected objects in homes, offices and factories
|
Overall, the EU's commitment to cybersecurity is reflected in its long-term budget, strengthened legislation, and comprehensive cybersecurity strategy. The EU aims to enhance its cybersecurity capabilities to ensure a safe and secure digital environment for its citizens and businesses by:
|
Legal Framework
The European Union has established a legal framework to address cybersecurity threats and promote cybersecurity measures.
Some of the key pieces of legislation in this framework include:
These pieces of legislation, along with other EU and national laws, form a comprehensive legal framework for cybersecurity in the EU. The framework seeks to promote cooperation and information-sharing between member states, and to establish minimum security and reporting requirements for organizations operating in the EU.
Some of the key pieces of legislation in this framework include:
- General Data Protection Regulation (GDPR): This Regulation sets out basic rules for the protection of personal data of individuals within the EU. It also requires organizations to take appropriate technical and organizational measures to protect personal data from unauthorized access, alteration, or destruction.
- Network and Information Security Directive (NIS Directive): The NIS Directive establishes security and reporting requirements for operators of essential services (such as energy, transport, and healthcare) and digital service providers (such as online marketplaces and cloud computing providers). It also requires member states to establish national cybersecurity strategies and computer emergency response teams (CERTs).
- Directive on Security of Network and Information Systems (NIS 2 Directive): This Directive updates the NIS Directive and aims to strengthen the cybersecurity of network and information systems across the EU. It introduces new security requirements for digital service providers and operators of essential services, and provides for increased cooperation and information-sharing between member states.
- Cybersecurity Act: The Cybersecurity Act creates a framework for EU-wide cybersecurity certification schemes for ICT products, services, and processes. It also strengthens the role of the European Union Agency for Cybersecurity (ENISA) in providing technical assistance and support to member states.
- eIDAS Regulation: The eIDAS Regulation sets out rules for the recognition of electronic identification and trust services across the EU. It provides a legal framework for electronic signatures, seals, timestamps, and electronic delivery services.
These pieces of legislation, along with other EU and national laws, form a comprehensive legal framework for cybersecurity in the EU. The framework seeks to promote cooperation and information-sharing between member states, and to establish minimum security and reporting requirements for organizations operating in the EU.
Regulation on Cybersecurity (EU 2019/881) "Cybersecurity Act"
|
As mentioned before, the Regulation on Cybersecurity (also known as the Cybersecurity Act) is a key piece of legislation in the EU legal framework on cybersecurity. It aims to enhance cybersecurity in the EU by establishing a framework for the certification of ICT products, services, and processes.
Under the Cybersecurity Act, the EU can develop and adopt European cybersecurity certification schemes that apply to specific categories of ICT products, services, and processes. The certification schemes are intended to help build trust in the security of ICT products and services and facilitate cross-border trade within the EU. The Cybersecurity Act also strengthens the role of the European Union Agency for Cybersecurity (ENISA) in providing technical assistance and support to member states. ENISA is responsible for developing guidelines and recommendations on cybersecurity, providing advice and assistance to member states in the event of cybersecurity incidents, and promoting cooperation and information-sharing among member states and with the private sector. In addition to the certification schemes and the role of ENISA, the Cybersecurity Act also establishes a framework for a European cybersecurity research and competence center and a network of national cybersecurity coordination centers. |
Overall, the Cybersecurity Act is an important component of the EU's legal framework on cybersecurity. It seeks to promote a common approach to cybersecurity across the EU, enhance trust and confidence in the security of ICT products and services, and facilitate cross-border trade in the digital single market.
Draft Regulation on EU Cyber Resilience Act
|
On September 15, 2022, the European Commission adopted the Cyber Resilience Act. A Proposal for Regulation to strengthen cybersecurity regulations in order to ensure that hardware and software products are more secure.
Hardware and software products are increasingly subject to successful cyberattacks, leading to an estimated global annual cost of cybercrime of €5.5 trillion by 2021. Two main objectives were identified aiming to ensure the proper functioning of the internal market:
|
Key aspects of the proposal include:
Read the Summary of the Opinion of the European Data Protection Supervisor.
In the Parliament, the file has been assigned to the Committee on Industry, Research and Energy (ITRE) and Nicola Danti (Renew, Italy) has been appointed as rapporteur. The report was adopted by the ITRE Committee with 61 votes to 1, with 10 abstentions on 19 July 2023. Committee amended to the Commission proposal. Here the text.
In Council, Member States’ representatives (Coreper) reached a common position on 19 July 2023, allowing the Council to enter in negotiations with the European Parliament.
Council notably removed the notion of "critical" from products with digital elements and deleted a substantial number of the products listed in the Annex III. Council introduced three categories of products, critical for essential entities as defined by the NIS2, that would fall under mandatory European cybersecurity certification by means of a delegated act. The Council moved the reporting of cybersecurity incidents and actively exploitable vulnerabilities from ENISA to the national Computer Security Incident Response Teams (CSIRTs) in a two-step process of an initial notification after 24 hours and a second one after 72 hours. Council proposes to postpone the application of the regulation to 36 months.
- Security and Update Obligations: Manufacturers are required to provide security support and software updates to address vulnerabilities, ensuring consumer protection and product cybersecurity.
- Uniform EU Cybersecurity Rules: The act aims to establish a single set of EU-wide rules, reducing cybersecurity incidents and enhancing consumer trust and data privacy.
- Conformity Assessment and CE Marking: Products with digital elements must undergo a conformity assessment process (self-assessment or third-party assessment, depending on the product category) to demonstrate compliance with cybersecurity requirements, resulting in a CE marking.
- Lifecycle Obligations and Market Surveillance: The proposal outlines obligations for the design, development, production, and surveillance of these products, including reporting obligations for manufacturers.
Read the Summary of the Opinion of the European Data Protection Supervisor.
In the Parliament, the file has been assigned to the Committee on Industry, Research and Energy (ITRE) and Nicola Danti (Renew, Italy) has been appointed as rapporteur. The report was adopted by the ITRE Committee with 61 votes to 1, with 10 abstentions on 19 July 2023. Committee amended to the Commission proposal. Here the text.
In Council, Member States’ representatives (Coreper) reached a common position on 19 July 2023, allowing the Council to enter in negotiations with the European Parliament.
Council notably removed the notion of "critical" from products with digital elements and deleted a substantial number of the products listed in the Annex III. Council introduced three categories of products, critical for essential entities as defined by the NIS2, that would fall under mandatory European cybersecurity certification by means of a delegated act. The Council moved the reporting of cybersecurity incidents and actively exploitable vulnerabilities from ENISA to the national Computer Security Incident Response Teams (CSIRTs) in a two-step process of an initial notification after 24 hours and a second one after 72 hours. Council proposes to postpone the application of the regulation to 36 months.
The Parliament confirmed the committee decision to enter into interinstitutional negotiations on 13 September 2023.
The co-legislators started trilogue negotiations on the file on 27 September 2023.
The co-legislators started trilogue negotiations on the file on 27 September 2023.
Draft Regulation on EU Cyber Solidarity Act
|
The European Commission proposed the EU Cyber Solidarity Act on April 18, 2023, to enhance the EU's ability to detect, prepare for, and respond to cybersecurity threats and attacks. Key elements of the proposal include:
The European Cyber Shield and Cyber Emergency Mechanism will be funded by the Digital Europe Programme (DEP), requiring an amendment to the Digital Europe Programme Regulation. The total budget for the Cyber Solidarity Act, including Member States' contributions, could reach €1.1 billion. In the European Parliament, the proposal has been assigned to the Committee on Industry, Research and Energy (ITRE), with Lina Gálvez Muñoz appointed as rapporteur. The European Economic and Social Committee (EESC) adopted its opinion on the Act on July 13, 2023. The Rapporteur's draft report, published on September 4, 2023, emphasizes:
The report is set for a vote in the ITRE Committee in November 2023. Meanwhile, the Council's Horizontal Working Party on Cyber Issues is examining the proposal. |
Draft Regulation on EU Cybersecurity Certification Schemes
|
On 18 April 2023, the Commission proposed a targeted amendment to the EU CyberSecurity Act (EU) 2019/8811 to allow for the adoption of European cybersecurity certification schemes for managed security services.
Member states’ representatives (Coreper) reached a common position on the proposed targeted amendment of the EU’s Cybersecurity Act (CSA) of 2019. Currently, only ICT products, services, and processes are covered under the Cybersecurity Act. The certification of managed security services is seen as an effective way to build trust in the quality of those services and facilitate the emergence of a trusted European cybersecurity service industry. The EU aims to raise the overall level of cybersecurity and encourage the development of trusted cybersecurity service providers to achieve this goal. The proposed amendment is in line with the Joint Communication 'EU Policy on Cyber Defence,' which announced the Commission's intention to explore the development of EU-level cybersecurity certification schemes for the cybersecurity industry and private companies. The Cyber Solidarity Act (see above), proposed in parallel to this Regulation, supports the gradual set-up of the EU-level cybersecurity reserve and the relevant cybersecurity services provided by "trusted providers," which correspond to managed security services in this proposal. |
Some Member States have already begun adopting certification schemes for managed security services, increasing the risk of fragmentation in the internal market for managed security services. The proposed amendment aims to prevent such fragmentation by creating European cybersecurity certification schemes for managed security services.
At the Parliament, the file has been allocated to the Industry Committee(ITRE). The rapporteur published her report on 7 September 2023 and she presented it during the ITRE committee meeting on 18 September 2023. While the IMCO committee published its opinion on 21 September 2023.
The ITRE rapporteur supports the Commission proposal to avoid that individual Member States continue adopting different certification schemes for managed security services to avoid fragmentation and further divergences. She aims for the complementarity between the xxx and the Cyber Solidarity Act, to allow for managed security services (i.e. ´trusted providers´ in the Cyber Solidarity Act) to play an important role in the future EU Cybersecurity Reserve.
In her report, she aims to clarify the definition of managed security services as well as their scope. In addition, she puts a stronger emphasis on addressing the skills gap and in supporting SMEs to benefit from appropriate financial support for addressing such challenge. The amendments tabled to the draft report were published on 21 September 2023. The vote in ITRE committee is foreseen on 25 October 2023.
Work at the Council has started and is ongoing. At its meeting on 15 November 2023, Coreper confirmed the agreement on the text of the above mentioned Regulation, as set out in Annex. Coreper also agreed that, on the basis of this text, negotiations could start with the European Parliament in the context of the ordinary legislative procedure.
At the Parliament, the file has been allocated to the Industry Committee(ITRE). The rapporteur published her report on 7 September 2023 and she presented it during the ITRE committee meeting on 18 September 2023. While the IMCO committee published its opinion on 21 September 2023.
The ITRE rapporteur supports the Commission proposal to avoid that individual Member States continue adopting different certification schemes for managed security services to avoid fragmentation and further divergences. She aims for the complementarity between the xxx and the Cyber Solidarity Act, to allow for managed security services (i.e. ´trusted providers´ in the Cyber Solidarity Act) to play an important role in the future EU Cybersecurity Reserve.
In her report, she aims to clarify the definition of managed security services as well as their scope. In addition, she puts a stronger emphasis on addressing the skills gap and in supporting SMEs to benefit from appropriate financial support for addressing such challenge. The amendments tabled to the draft report were published on 21 September 2023. The vote in ITRE committee is foreseen on 25 October 2023.
Work at the Council has started and is ongoing. At its meeting on 15 November 2023, Coreper confirmed the agreement on the text of the above mentioned Regulation, as set out in Annex. Coreper also agreed that, on the basis of this text, negotiations could start with the European Parliament in the context of the ordinary legislative procedure.
The EU Directive (NIS 2)
|
On 14 December 2022, EU adopted the EU Directive on Cybersecurity NIS 2.
The first EU-wide legislation on cybersecurity was the Directive on Security of Network and Information Systems (NIS Directive), which came into effect in 2016. The NIS Directive aimed to establish a common level of cybersecurity across the EU and improve the cybersecurity preparedness of operators of essential services and digital service providers. The NIS Directive required EU Member States to implement national cybersecurity rules and to designate national authorities responsible for cybersecurity. The NIS Directive was later reviewed and updated, resulting in the new Directive on measures for high common level of cybersecurity across the Union, also known as the The NIS 2 Directive builds on the NIS Directive and introduces several changes and new provisions. |
Here are some of the key differences between the NIS Directive and NIS 2:
1. Scope: The NIS 2 Directive extends the scope of the NIS Directive to cover a broader range of entities, including more digital service providers and certain online platforms. It also introduces new provisions for the cybersecurity of certain critical sectors, such as healthcare and transport.
2. Cooperation and information-sharing: The NIS 2 Directive strengthens the cooperation and information-sharing requirements between EU Member States and with the European Union Agency for Cybersecurity (ENISA).
3. Incident reporting: The NIS 2 Directive introduces new incident reporting requirements for digital service providers and certain online platforms. These entities will need to report major cybersecurity incidents to national authorities within specific timeframes.
4. Cybersecurity requirements: The NIS 2 Directive sets out new and more specific cybersecurity requirements for operators of essential services and digital service providers. It also introduces new provisions for the security of the supply chain, including requirements for third-party risk management.
Overall, the NIS 2 Directive aims to further improve the EU's cybersecurity resilience and ensure a high level of cybersecurity across the EU.
1. Scope: The NIS 2 Directive extends the scope of the NIS Directive to cover a broader range of entities, including more digital service providers and certain online platforms. It also introduces new provisions for the cybersecurity of certain critical sectors, such as healthcare and transport.
2. Cooperation and information-sharing: The NIS 2 Directive strengthens the cooperation and information-sharing requirements between EU Member States and with the European Union Agency for Cybersecurity (ENISA).
3. Incident reporting: The NIS 2 Directive introduces new incident reporting requirements for digital service providers and certain online platforms. These entities will need to report major cybersecurity incidents to national authorities within specific timeframes.
4. Cybersecurity requirements: The NIS 2 Directive sets out new and more specific cybersecurity requirements for operators of essential services and digital service providers. It also introduces new provisions for the security of the supply chain, including requirements for third-party risk management.
Overall, the NIS 2 Directive aims to further improve the EU's cybersecurity resilience and ensure a high level of cybersecurity across the EU.
Key points of the Directive NIS 2
The directive applies principally to medium-sized and large entities operating in the following sectors of high criticality as defined in Annex I:
- Energy:
- electricity, including production, distribution and transmission systems and charging points;
- district heating and cooling;
- oil, including production, storage and transmission pipelines;
- gas, including supply, distribution and transmission systems and storage; and
- hydrogen.
- Transport by air, rail, water and road.
- Banking and financial market infrastructures such as credit institutions, operators of trading venues and central counterparties.
- Health, including healthcare providers, manufacturers of basic pharmaceutical products and critical medical devices, and EU reference laboratories.
- Drinking water.
- Waste water.
- Digital infrastructure, including providers of data centre services, cloud computing services, public electronic communications networks and publicly available electronic communications services.
- ICT managed services (business-to-business).
- Space.
- Public administration at the central and regional level, excluding judiciary, parliaments, and central banks. However, it does not apply to public administration entities that carry out activities in the areas of national security, public security, defence or law enforcement.
It also applies to other critical sectors, as defined in Annex II:
- postal and courier services;
- waste management;
- chemical manufacturing, production and distribution;
- food production, processing and distribution;
- manufacturing, specifically medical devices, computer, electronic and optical products, certain electrical equipment and machinery, motor vehicles and other transport equipment;
- digital providers of online marketplaces, search engines and social networks; and
- research organisations.
Roles and obligation of Member States
Every Member State must adopt a national strategy to achieve and maintain a high level of cybersecurity in the critical sectors, including:
- a governance framework clarifying the roles and responsibilities for relevant stakeholders at the national level;
- policy addressing the security of supply chains;
- policy on managing vulnerabilities;
- policy on promoting and developing education and training on cybersecurity; and
- measures to improve cybersecurity awareness among citizens.
Role of the Teams charged on Computer security incident response (CSIRTs)
The Directive sets up a network of national "Computer security incident response teams" ( CSIRTs to promote swift and effective operational cooperation. CSIRTs provide technical assistance to entities, including by:
- monitoring and analysing cyber threats, vulnerabilities, and incidents at the national level;
- providing early warnings, alerts, announcements and information to the entities concerned and to other stakeholders on cyber threats, vulnerabilities and incidents, if possible in near-real time;
- responding to incidents and providing assistance where applicable;
- collecting and analysing forensic data and providing dynamic risk and incident analysis and situational awareness on cybersecurity; and
- providing, on request, proactive network and information system scanning to detect vulnerabilities with a potential significant impact
The European Union Agency for Cybersecurity (ENISA) publishes a map of national Coordinated Vulnerability Disclosure (CVD) policies in the EU Member States and makes recommendations.
Member States are charged to:
- designate one of their CSIRTs to coordinate the disclosure of vulnerabilities discovered in ICT products or services; and
- ensure that people in the Member States are able to report vulnerabilities, anonymously if requested.
Cooperation group
The Directive sets up a cooperation group to support and facilitate strategic cooperation and information exchange. It is composed of representatives of Member States, the European Commission and ENISA. Where appropriate, the cooperation group may invite the European Parliament and representatives of relevant stakeholders to participate in its work.
The European cyber crisis liaison organisation network
The European cyber crisis liaison organisation network (EU-CyCLONe) is a network comprising representatives of Member State cyber crisis management authorities, as well as the Commission, in cases where a potential or ongoing large-scale cybersecurity incident has or is likely to have a significant impact on the sectors covered by the directive. In other cases, the Commission shall participate in the activities of the network as an observer. The network supports the coordinated management of large-scale cybersecurity incidents and crises at the operational level and ensures the regular exchange of information among Member States and EU institutions, bodies and agencies.
The network is tasked, among other things, with:
Reporting
Entities must notify their CSIRT or relevant authority of any incident that:
Supervision and enforcement
The directive provides for remedies and sanctions to ensure enforcement.
Peer reviews
Peer reviews are set up with a view to learning from shared experiences, strengthening mutual trust, achieving a high common level of cybersecurity, and enhancing Member States’ cybersecurity capabilities and policies necessary to implement this directive. These reviews entail physical or virtual on-site visits and off-site exchanges of information. Participation in these peer reviews is voluntary.
The Directive sets up a cooperation group to support and facilitate strategic cooperation and information exchange. It is composed of representatives of Member States, the European Commission and ENISA. Where appropriate, the cooperation group may invite the European Parliament and representatives of relevant stakeholders to participate in its work.
The European cyber crisis liaison organisation network
The European cyber crisis liaison organisation network (EU-CyCLONe) is a network comprising representatives of Member State cyber crisis management authorities, as well as the Commission, in cases where a potential or ongoing large-scale cybersecurity incident has or is likely to have a significant impact on the sectors covered by the directive. In other cases, the Commission shall participate in the activities of the network as an observer. The network supports the coordinated management of large-scale cybersecurity incidents and crises at the operational level and ensures the regular exchange of information among Member States and EU institutions, bodies and agencies.
The network is tasked, among other things, with:
- coordinating the management of large-scale cybersecurity incidents and crises and supporting decision-making at the political level;
- increasing preparedness;
- developing a shared situational awareness; and
- assessing the consequences and impact of large-scale cybersecurity incidents and crises and proposing possible mitigation measures.
Reporting
Entities must notify their CSIRT or relevant authority of any incident that:
- can cause or is capable of causing severe operational disruption or financial loss for the entity;
- it has affected or could affect others by causing considerable material or non-material damage.
Supervision and enforcement
The directive provides for remedies and sanctions to ensure enforcement.
Peer reviews
Peer reviews are set up with a view to learning from shared experiences, strengthening mutual trust, achieving a high common level of cybersecurity, and enhancing Member States’ cybersecurity capabilities and policies necessary to implement this directive. These reviews entail physical or virtual on-site visits and off-site exchanges of information. Participation in these peer reviews is voluntary.
Sanctions against cyberattacks
The Council established a framework which allows the EU to impose targeted sanctions to deter and respond to cyberattacks which constitute an external threat to the EU or its member states.
More specifically, this framework allows the EU for the first time to impose sanctions on persons or entities that are responsible for cyberattacks or attempted cyberattacks, who provide financial, technical or material support for such attacks or who are involved in other ways. Sanctions may also be imposed on other persons or entities associated with them.
Restrictive measures include:
- a ban on persons travelling to the EU
- an asset freeze on persons and entities
The first ever sanctions for cyberattacks were imposed on 30 July 2020.